One-paragraph Summary (TL;DR)
A recent incident involving a retail business highlights a critical shift in social engineering: attackers are now using AI-cloned voices to divert payments, moving past traditional email phishing. While technical filters remain necessary, they cannot see or block a conversation between two humans where trust is the primary exploit. This post argues that organizations must move beyond the “weakest link” mentality to build durable behavioral proficiency and verification protocols that survive high-pressure, high-fidelity attacks.
Imagine receiving a call from your boss. The tone, the cadence, and even the emotional cues are unmistakable. They ask for an urgent wire transfer to a new account to secure a critical vendor contract. This is exactly what happened to a retail business recently reported to the INCIBE 017 helpline on February 3, 2026. This wasn’t a failure of a firewall; it was a precise attack on human trust through the industrialization of impersonation.
The reconnaissance phase: silent calls as data collection
- Many victims of voice cloning report receiving “silent calls” in the days leading up to the attack.
- These aren’t technical glitches; they are often reconnaissance attempts to gather voice samples for AI training.
- With just three to ten seconds of audio, easily harvested from a silent call or social media, AI can now create a voice clone with nearly 90% accuracy.
Moving beyond mandatory compliance
- Traditional security has focused on “checking the box” for mandatory training, which often fails in high-stress moments.
- Real-world social engineering exploits human psychology by creating high-pressure situations where the victim feels they must act fast to “save the day”.
- We must shift the focus from simple awareness to measurable behavior change, treating the human defense layer as a defensible system.
The strategy of the transformation partner
- Positioning security leaders as strategic allies involves providing expert guidance on capability gaps rather than just technical checklists.
- Establishing a robust human defense layer requires unifying fragmented tools into a system that provides real-time visibility into how teams navigate risk.
Key insight: Trust is no longer a given in digital communication; it is a variable that must be verified. In an AI-driven landscape, the perimeter has shifted from the network edge to the individual’s decision-making process. Behavioral proficiency is the only control capable of adapting to the nuance of a synthetic voice in real-time.
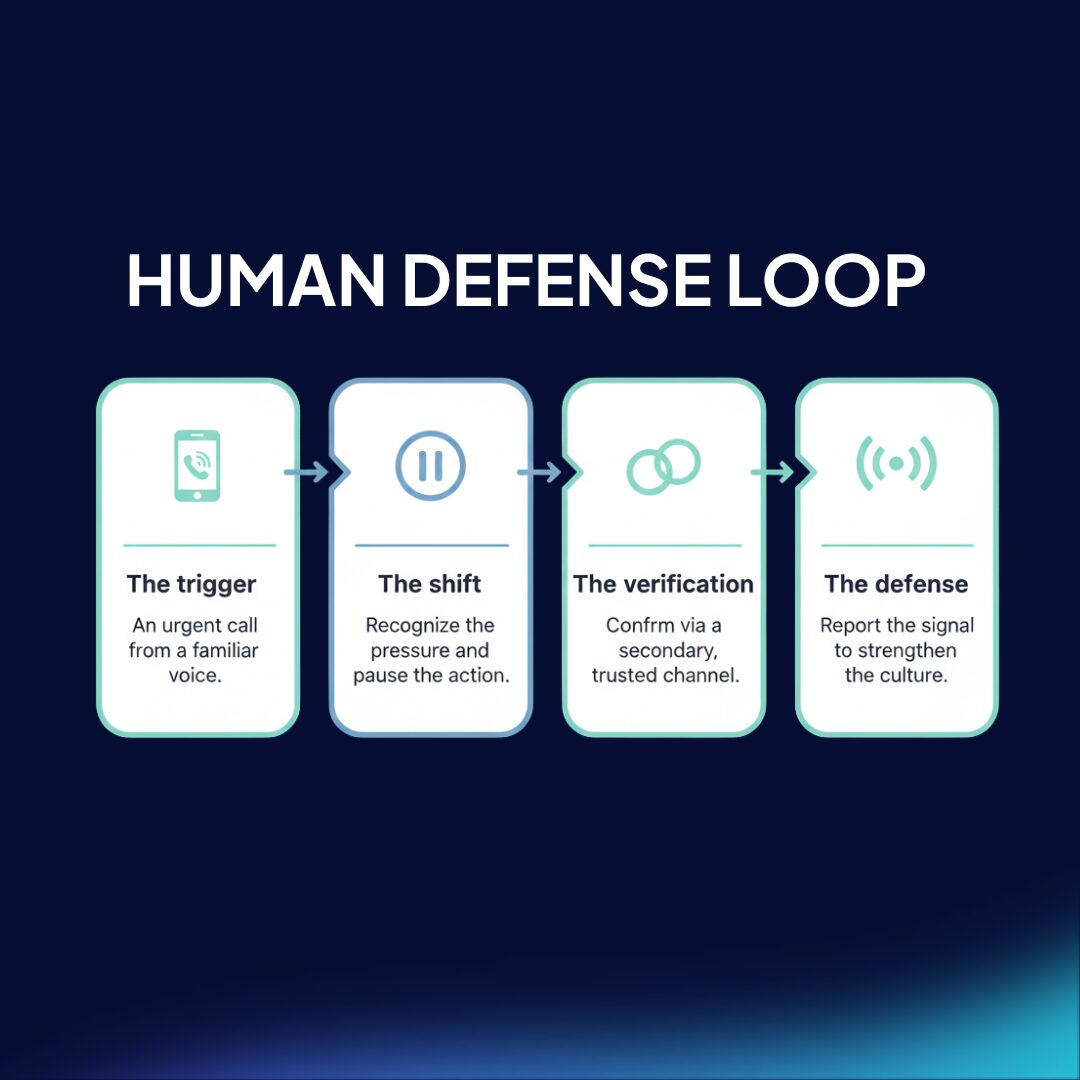
Practical Implications: Based on the recent INCIBE incident and industry best practices, leaders should implement these operational protocols:
- Manual redial rule: If a call involves financial changes, hang up immediately and manually dial the person’s known number from your contacts.
- Challenge-response phrases: Use pre-agreed “safe words” or security questions for sensitive transactions that cannot be found via social media or internet searches.
- Verify through secondary channels: Always confirm urgent requests via a different, trusted platform (e.g., encrypted messaging or video) before acting.
- Non-judgmental reporting: Encourage teams to report “silent calls” or suspicious requests immediately, framing these as opportunities to strengthen organizational skill rather than failures.
Conclusion: Security starts with trust, but it is proven by capability. As AI continues to lower the barrier for sophisticated impersonation, our strongest defense is not more technology, but a culture where every person is an empowered, proactive defender.